Adopting Cloud no longer has a security barrier. It is however a shared responsibility between the cloud provider and tenant. It is important that the tenant understands this principle so they properly secure their resources.
Securing IaaS is not just about just securing VMs but also the networking and services like storage. It is also about securing multiple clouds as many customers have a multi-cloud strategy. While things like malware protection need to be applied in the cloud the application is different in the cloud. Key challenges specific to cloud are:
- Visibility and Control
- Management Complexity (a mix of IaaS, PaaS and SaaS components)
- Rapidly Evolving Threats (you need a solution optimized for cloud as things are more dynamic)
Microsoft ensures that Azure is built on a Secure Foundation by enforcing physical, infrastructure and operational security. Microsoft provides the controls but the customer or tenant is responsible for Identity & Access, Information Protection, Threat Protection and Security Management.
10 Ways Azure Security Center helps protect IaaS deployments
1 Monitor security state of cloud resources
- Security Center Automatically discovers and monitors Azure resources
- You can secure Enterprise and 3rd party clouds like AWS from Security Center
Security Center is built into the Azure Panel so no additional access is required. If you select the Data Collection policy you can automatically push the monitoring agent. This agent is the same as the Operations Management Agent. When you setup Data Collection you can set the level of logging required.
Security Center comes with a policy engine that allows you to tune policies via subscription. For example you can define one policy posture for production and another for dev and test.
2 Ensure VMs are configured in a certain way
- You can see system update status, Antimalware protection (Azure has one that is built in for free), OS and web configuration assessment (e.g. IIS assessment against best practise confirms)
- It will allow you to fix vulnerabilities quickly
3 Encrypt disks and data
4 Control Network Traffic
5 Use NSGs add additional firewalls
6 Collect Security Data
- Analyze and search security logs from many sources
- Security Center allows you to integrate 3rd party products like Qualys scans as well for assessment for other applications and compliance issues. Security Center monitors IaaS VMs and some PaaS components like web apps.
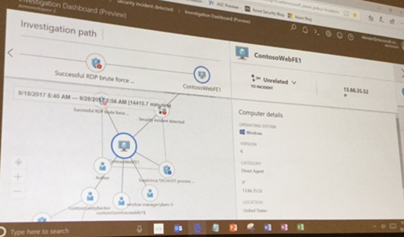
Security Center provides a new dashboard for failed logon attempts on your VMs. The most common attack on cloud VMs are RPD brute force attacks. To avoid this you can use Just-in-Time access so that port 3389 is only open for a window of time from certain IPs. These are all audited and logged.
Another attack vector is Malware. Application whitelisting allows you to track for good behaviour vs. blocking the bad. Unfortunately it has been arduous to apply.
7 Block malware and unwanted applications
Security Center uses the adaptive algorithm to understand what applications are running to develop a set of whitelists. Once you are happy with lists you can move to enforcement.
8 Use advanced analytics to detect threats quickly.
Security Center looks at VMs and network activity and leverages Microsoft’s global threat intelligence to detect threats quickly. This leverages machine learning to understand what is normal activity statistically to identity abnormal behavior.
9 Quickly assess the scopes and impact of the attack
This is a new feature that graphically displays all the related components that were involved in an attack.
10 Automate threat response
Azure uses Logic Apps to automate responses which allows you to trigger workflows form and alert to enable conditional actions. In addition there is a new malicious map that identifies known malicious IPs by region with related threat intelligence.
The basic Policy for Security Center is free so there is no reason to not have more visibility on what is vulnerable in your environment.
For more information check out








No comments:
Post a Comment